Cryptography is taking data & hidden that data in some way so that other people can’t see that & then bringing the data back. This unreadable format is called ciphertext. The original, readable data is called plaintext.
Encryption & Decryption:
Transforming data from plaintext to ciphertext know as encryption.
Transforming data from ciphertext to plaintext know as decryption.
The Oldest cryptography is Ceaser Cypher. Ceaser Cypher is a simple encryption technique for hiding messages. Here’s what you do:
Shifting the Alphabet:
choose a shift value basic means how many time you want to rotate the alphabets for example
A B C D E -> alphabets
C D E A B -> shifting alphabets of 2 rotation
suppose we have to encrypt word ACE, so the encrypted word will be CEB.
Drawback of Ceaser Cypher:
- There are only 26 possible Caesar Ciphers (one for each shift value). This means an attacker can easily try all possible shifts and crack the code with minimal effort.
- If an attacker has even a small portion of the original message (plaintext) along with the encrypted message (ciphertext), they can easily determine the shift value and decrypt the rest.
The Vigenère cipher stands as a significant advancement in cryptography due to its innovative combination of an algorithmic approach with a secret key for data encryption.
Vigenère cipher is not designed for non-text data means data which is in picture format or in database or credit card information is not going to be encrypted.
XOR encryption:
XOR encryption is a type of symmetric encryption that uses a bitwise XOR operation for both encryption and decryption.
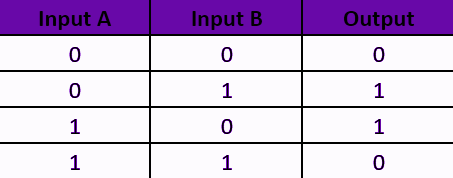
Suppose you want to encrypt letter MANOJ using 5-Bit key i.e. 11010.
M A N O J
01001101 01000001 01001110 01001111 01001010
11010110 10110101 10101101 01101011 10110101 +
10011011 11110100 00100101 00100100 11111111 =
As you can see about by adding 5-Bit key to our letter the plaintext got ciphertext and to decrypt the above data we are going to use the same key and get our data in readable characters.
It’s crucial to understand that while this example demonstrates the XOR concept, a 5-bit key is extremely weak for real-world encryption. With only 32 possible key combinations, it’s easily crackable using brute-force methods where someone tries every single key combination until they find the one that decrypts the message.
Symmetric encryption:
Symmetric encryption is a type of encryption where a single secret key is used for both encryption and decryption. It’s like having one key that can both lock and unlock a door.
Both the sender and receiver of the information share a common secret key. This key is like a password that needs to be kept confidential.
The sender uses the key and an encryption algorithm to scramble the original message (plaintext) into an unreadable format (ciphertext).
The receiver, who also possesses the same secret key, uses the decryption algorithm and the key to transform the ciphertext back into the original plaintext message.
Used in protocols like Secure Sockets Layer (SSL/TLS) to encrypt communication between web browsers and servers.
Symmetric encryption offers a good balance between speed and security for various applications. However, key management remains a crucial aspect to ensure the effectiveness of this method.
| common symmetric encryption algorithms | Key Size | No. of Rounds | Block Size |
| DES(Data Encryption Standard) | 56-Bit | 16 Rounds | 64-Bit |
| Triple DES | 56*3=168-Bits | 16 Rounds | 64-bit |
| Blowfish | 32-448 Bits | 16 Rounds | 64-Bit |
| AES(Advanced Encryption Standard) | 128,192 or 256 Bits | 10,12 or 14 Rounds | 128-Bits |
| RC4(Steaming Cipher) | 40-2048-Bits | 1 Round | 1-Bit at a time |
Asymmetric encryption:
Asymmetric encryption, also known as public-key cryptography, is a type of encryption that uses a pair of mathematically linked keys for encryption and decryption. This differs from symmetric encryption, which uses a single secret key for both tasks.
- Public Key: This key is freely available to anyone who wants to send you encrypted messages. You can publish it on your website, include it in your email signature, or distribute it however you choose. Think of it like a public mailbox anyone can put things into.
- Private Key: This key is kept strictly confidential and should never be shared with anyone. It’s like the only key that can open your personal mailbox and retrieve the messages inside.
Encryption: When someone wants to send you a secure message, they use your publicly available public key to encrypt the message. The encryption process mathematically transforms the message (plaintext) into an unreadable format (ciphertext) using the public key. This ensures only someone with the matching private key can decrypt it.
Decryption: Once you receive the encrypted message (ciphertext), you use your own private key to decrypt it. The decryption algorithm reverses the mathematical transformation applied during encryption, and you can access the original message (plaintext).
Asymmetric encryption offers a powerful solution for secure communication and digital signatures. While it’s slower than symmetric encryption, it addresses the key distribution challenge and enables functionalities like digital signatures. In many applications, a hybrid approach is used, combining asymmetric encryption for secure key exchange with symmetric encryption for faster bulk data encryption.
RSA (Rivest–Shamir–Adleman),DSA (Digital Signature Algorithm),Elliptic Curve Cryptography (ECC),Diffie-Hellman Key Exchange are example of Asymmetric encryption.
Cryptography Attack
Brute Force Attack: This brute-force method involves systematically trying every possible key combination until the correct one is found. It’s like trying every lock combination until you find the one that opens the door. While effective against weak encryption, it becomes computationally impractical for strong ciphers with vast key spaces.
Man-in-the-Middle Attack (MitM): Imagine an eavesdropper on a phone call. In a MitM attack, the attacker intercepts communication between two parties, potentially stealing data or even altering it undetected. Public Wi-Fi networks can be vulnerable to such attacks.
Dictionary Attack: A dictionary attack brute-forces passwords or encryption keys by trying common words, phrases, and variations. This preys on weak passwords like dictionary words or birthdays.
Rainbow Table Attack: Rainbow tables are like pre-computed cheat sheets for attackers trying to crack passwords. Instead of guessing every combination one by one, attackers can use these tables to quickly find the match for a hashed password (a scrambled version of your password stored for security).