IAAA stands for Identification, Authentication, Authorization, and Access Control. These four pillars work together to create a robust security system, ensuring only the right people have access to the right information. Let’s break down each pillar:
- Identification: This establishes who you are in the digital world. It could be your username, email address, employee ID, or even a biometric identifier like a fingerprint.
- Authentication: Once you identify yourself, authentication verifies that you are who you claim to be. This typically involves providing a credential, like a password, PIN, or security token. Multi-factor authentication (MFA) strengthens this by requiring proof from multiple categories (e.g., password + fingerprint).
- Authorization: Authentication gets you in the door, but authorization determines what you can do once inside. Are you a visitor with limited access, or an administrator with full control? Authorization defines these permission levels.
- Access Control: This enforces the authorization rules. Think of it as a security guard checking IDs at a club. Access control ensures only users with the appropriate permissions can access specific resources or functionalities within a system.
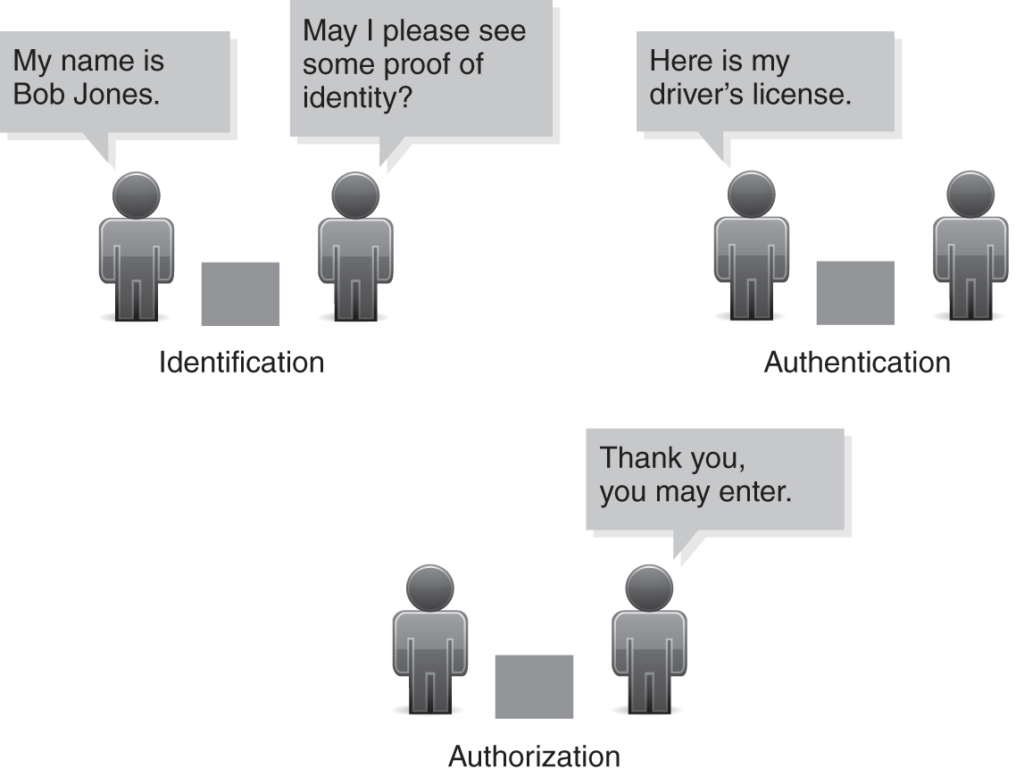
Identification: The text “My name is Bob Jones” signifies the identification stage. Bob Jones is identifying himself to the system.
Authentication: The text “May I please see some proof of identity?” represents the authentication stage. The system is asking Bob Jones for proof to verify his claimed identity. In a real-world scenario, this proof could be a password, PIN, fingerprint scan, or a security token.
Authorization (not shown in the image): While not explicitly shown in the image, authorization is the third pillar of IAAA. Once Bob Jones is authenticated, the system would determine his authorization level. This authorization level determines what actions Bob Jones can perform within the system. For instance, he might be authorized to view account balances, transfer funds, or pay bills, depending on his account type and any specific permissions granted.
Access Control (not shown in the image): Access control is the final pillar of IAAA and enforces the authorization policies. This isn’t directly represented in the image, but imagine after successful authentication, the system acts like a gatekeeper. It grants Bob Jones access to specific functionalities and information based on his authorization level.
Overall, the image depicts the initial steps (identification and authentication) of the IAAA framework.
Why is IAAA Important?
By implementing a strong IAAA framework, organizations can:
- Prevent unauthorized access: IAAA helps prevent data breaches and cyberattacks by ensuring only authorized users can access sensitive data and systems.
- Maintain data integrity: Limiting access through IAAA protects data from unauthorized modifications or deletions.
- Improve accountability: Tracking user access through IAAA helps identify who accessed what information and when, which is crucial for security audits and investigations.
Let’s explore how IAAA plays a crucial role in some common everyday activities:
Online Banking
Social Media Platforms
Online Banking:
- Identification: You enter your username or account number (identification).
- Authentication: You verify your identity with a password or PIN (authentication). Multi-factor authentication (MFA) might require a fingerprint scan or a code sent to your phone for an extra layer of security.
- Authorization: Based on your account type (authorization), you can view account balances, transfer funds, or pay bills. An administrator might have additional permissions to manage user accounts or access broader financial data.
- Access Control: The system enforces these permissions (access control). You can only access features and information based on your account type and any additional authorizations granted.
This example highlights how IAAA safeguards your online financial information. Feel free to ask any questions you might have about IAAA, leave a comment below requesting an explanation for “Social Media Platforms.” By understanding IAAA, you can become a more informed and secure online banking user.